Introducing Webscale Account Hierarchies
Note:
Webscale account hierarchies are an advanced feature.Overview
Webscale accounts (parent accounts) can optionally be configured with one more sub-accounts to create account hierarchies. This hierarchial relationship naturally matches the structure Webscale Partners use to manage their various eCommerce clients. In concert with Webscale role-based access, this hierarchy allows Partners to grant a user access to multiple sub-accounts while also being able to limit their access in each account.
Create a sub-account
In order to create a sub-account, you must have accepted an invitation to the Entitlement administrator role, defined in the Webscale-managed account Root. This role is managed by Platform Operations.
This capability is only available through the Webscale API. To successfully create a sub-account, the API request adheres to the following format:
POST /v2/accounts
{ "name": <sub-account-name> }
where sub-account-name is a unique account name. If it is already in use, a 409 status code will be returned and you’ll be ask to use a different name.
Note:
The parent of the sub-account is inferred from the account in which you are authenticated when the API request is made. Setting the parent account directly is not supported. The account you are authenticated into can be found by cross-referencing theaccount attribute from GET /v2/users/self/authorization with GET /v2/accounts.
Account hierarchies can have unbounded depth, allowing sub-accounts to also serve as parent accounts to yet more sub-accounts.
Grant access to the account
Sub-accounts will be created with their own Account owner role that limits which users are permitted to create roles in the account. By default, no users will be invited to this role unless done so by a Webscale Account owner administrator.
By default, when a custom role is created in an account, permission to retrieve the account is automatically added. This means to grant access to a sub-account, you need to invite a user to a role defined in the sub-account, including Account owner.
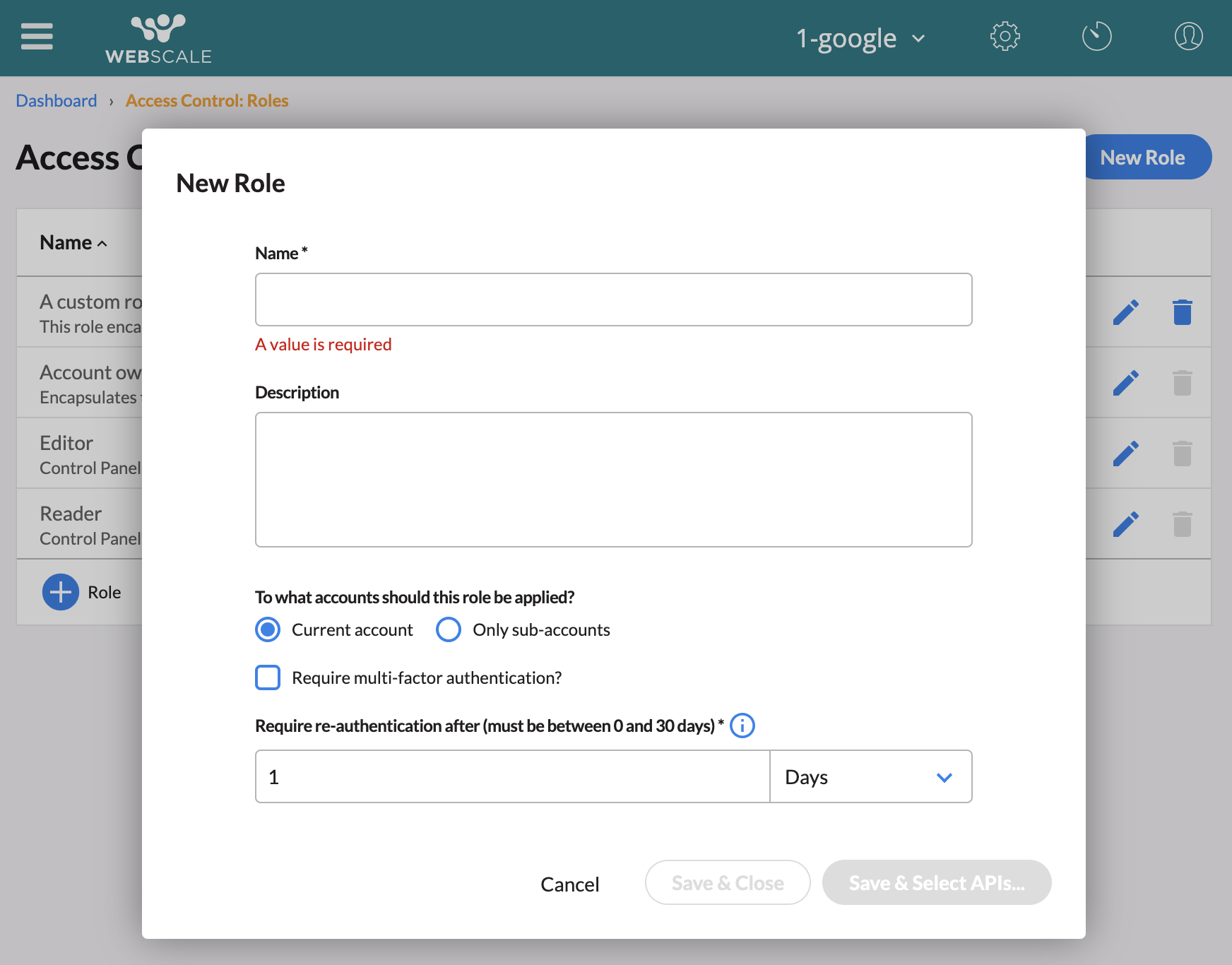
A role, and its permissions, can only be assumed by users that have accepted an invitation and are authenticated into the account in which the role was created. It is also possible to make a role assumable only in sub-accounts, meaning the user must be authenticated into any sub-account of the account in which the role was created in order to assume it. To do so, select the ‘Only sub-accounts’ option for ‘To what accounts should this role be applied?’ when creating a role.
Warning:
Roles applied in sub-accounts will be applied to all sub-accounts of the parent account.Remove access to the account
A user can be prevented from accessing a sub-account by revoking their invitations to roles in the sub-account and any roles defined in the parent account that apply to sub-accounts.
Feedback
Was this page helpful?
Glad to hear it! Have any more feedback? Please share it here.
Sorry to hear that. Have any more feedback? Please share it here.